Executive summary
Pests is the collective term we use to describe
non-viral malicious code - trojans, remote administration tools, hacker
tools, and spyware. Such code can stealthily gain access to and hide on
computer systems, bypassing traditional security measures such as
anti-virus, firewalls, and intrusion detection systems.
Pests can allow unauthorized users to breach firewalls
and access sensitive data by assuming the identity of authorized users.
Pests can then allow unauthorized third parties and disgruntled insiders
to access electronic assets (customer database, financial records,
intellectual property, trade secrets), compromise existing security,
destroy customer confidence, and expose individuals and organizations to
litigation.
Pests are fundamentally different from viruses, in
that they are self-contained programs rather than code fragments, and so
the technology required to detect and remove them is also fundamentally
different from anti-virus software. All pests share these common
characteristics: most people don't know anything about them, didn't invite
them in, don't know they are present, and don't want them in their system.
That is the heart of the problem. With thousands of files in today's
computers, no one could be expected to know what every single one does.
And, without the technology to help find pests, they can live and thrive
in your system for a long time before anyone finds out they're there - by
which time it may be too late.
Pests have the potential to create even greater damage
than viruses - including significant loss of business, legal liability,
and public relations nightmares
Protecting your systems against pests
PestPatrol picks up on the protection of your network
where current products leave off. It is designed to be used in
conjunction with anti-virus software, and has little to no impact on
system performance. PestPatrol, used in conjunction with an anti-virus
product, offers comprehensive and reliable protection against stealthy
malicious code that can result in downtime, loss of employee
productivity and legal liability.
A recent example of why additional protection beyond
anti-virus was the December 2001 outbreak of BadTrans B. Every anti-virus
company came out with a 'quick fix' to detect and remove the worm itself,
but did you know that the worm left behind a key logger that may still be
hidden on systems you thought were clean? PestPatrol would have found and
removed it.
Pest behavior and impact
Pests can do anything that software can do. Here are
just a few examples:
-
If your PC has ever locked up for no reason, the
CD-ROM drive has started to turn, or you've mysteriously lost files, you
could unknowingly have downloaded a RAT (remote administration tool),
enabling a hacker to control your machine without you ever knowing. Back
Orifice and Sub Seven are well known RATs.
-
If a disgruntled ex-employee plants a key logger on
critical systems before he's terminated, he can access confidential data
long after he's gone by capturing keystrokes for passwords. This is what
the key logger left behind by the trojan incorporated into the
BadTrans.B worm was programmed to do.
-
And, how would you like to discover that some company
has secretly planted spyware on your machine and has been following your
surfing habits and transmitting this information to an outside source?
No network administrator would be happy to find out
that intellectual property, customer data or even ownership of the
corporate web site has fallen into someone else's (unauthorized) hands.
Unlike viruses, however, there can be 'good' pests.
That is to say, tools such as password cracking programs are an important
part of the system administrator's toolkit, but in the wrong hands,
password crackers can allow unauthorized individuals to access
confidential data unchallenged. PestPatrol deals with this "gray area" by
enabling you to detect the presence of such a tool only if it's on a PC
where you would not expect to find it - in the accounting or sales
departments, for example
Why are pests on the rise?
Many factors conspire to make today's computer systems
a fertile environment for pest growth.
-
Users have changed. A decade ago, it seemed
that many users were fascinated by the details of their computer's
operation. Many knew that the size of COMMAND.COM in DOS 5.0 was 47,485
bytes. But today's users tend to regard computers as just another tool
to help them do their job, so there is less interest in the details of
what is going on behind the scenes. This simply means that, should
problem software be inadvertently introduced to a machine, the number of
users that are equipped to realize what has happened and deal with it is
a much smaller proportion of the total user population.
-
Operating systems are more complex. A decade
ago, DOS consisted of COMMAND.COM and two hidden system files, and could
fit on a low-capacity floppy. Today, the Windows directory on a typical
Windows 98 machine is likely to have 200 or more directories, 4,500 or
more files, and use 600 Mb or more. Today, no user could be expected to
know what every file in their computer does, where it came from, or if
it is even needed.
-
New software cannot be readily inspected prior to
installation. A decade ago, nearly all software introduced to a
machine was installed from a floppy disk. It was a simple matter to
determine the immediate source of that software, and to scan it for
viruses. Today, nearly all software is introduced to a machine via the
Internet. The transfer process might reveal the overall setup package,
but not its components. Even the size of the basic component often
cannot be determined with precision. And any kind of security check of
the installation package cannot usually be done prior to installation.
-
Software is installed in obscure ways. A decade
ago, software installations involved little more than creating a
directory and copying some files. Not until DOS 6 were operating system
files even compressed. Today, the exact process followed by an installer
is hidden by both the installation package (often a single file contains
dozens or hundreds of individual files) and installation procedure (an
installer may or may not enumerate files as they are extracted.)
Sometimes, as in the case of an ActiveX, Javascript, or VBScript
component on a web page, there is no evident installation process at
all: the software is simply transferred, installed and run, sometimes
without any user interaction at all.
-
Trusted sources can no longer be determined. A
decade ago, users were counseled to avoid viruses by only installing
software from trusted sources, and to not accept software from untrusted
sources. Users of a decade ago might call local Bulletin Boards (BBSs),
but would rarely make long distance calls to BBSs across the country, or
make international calls. And at 2400 baud, users spent some time
judging the potential value of software before downloading. Today, all
of the world's software is a local call away, via the Internet, and can
be accessed 30 to 1,000 times faster than it was a decade ago.
-
There is more problem software. Problem
software, such as viruses, does not become extinct just because it is
hunted. Every piece of malicious code that has ever been distributed
probably still lives, somewhere. In short, the evil that men do lives
long after they are gone.
The real problem is that the rate of emergence of
pests is increasing. The table and graph below report on the growth of
pests in both number of megabytes of pests and total number, by creation
date. These values come from the PestPatrol database, available for
examination at
http://pestpatrol.com/products/pestpatrol/pestdatabase.asp.
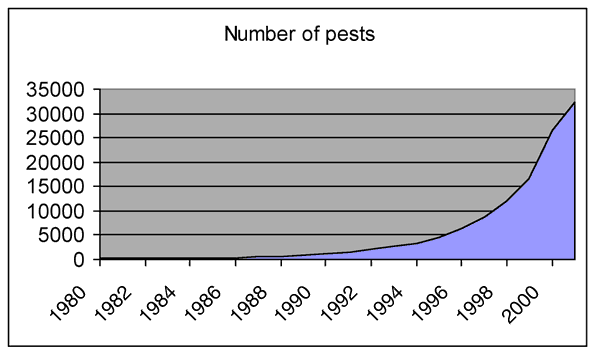
Figure 1: The number of pests has increased rapidly
over the past few years.
Anti-virus (AV) requires a different approach
|
Anti-virus vendors have added detection capabilities
for some high-profile pests. They just haven't added it very
well or with any degree of thoroughness or consistency. There
are two main reasons for this:
There have been many pests in the news recently. In
fact, they sometimes seem to be "stealing the show" from
viruses. For example, the "SubSeven Defcon8 2.1 backdoor trojan"
is a trojan, not a virus.
Anti-virus is not enough
Anti-virus software detects some pests, particularly those that
have made the news. But generally, the pest detection rates of
anti-virus software are pretty low. To illustrate this, we asked
the National Software Testing Laboratory (NSTL) to test
PestPatrol's pest detection capabilities against the three major
anti-virus software packages - Norton AntiVirus, McAfee, and PC-Cillin.
Here is a summary of their findings:
"PestPatrol clearly detects more pests in every
category than any other product tested by finding 86% of the
pests. PC-Cillin 2000 came in a distant second, finding 55%.
Although no product, in its default state, detected every
available pest, it is clear which product provides the better
protection.
"Our testing indicates that pest detection, unlike
virus detection, has not been given strong enough attention by
the computer industry. This may be due to the fact that pests
tend to run silently, and users often don't even know that their
systems are infected. So there is no big outcry by infected
owners for remediation or prevention. As more people become
aware of pests and see the damage that they can do, there should
be increased demand for effective products to detect and clean
pests.
"Currently, products tend to do their best detection
with trojan-type pests - detecting a larger percentage of them.
Pests used for hacking or performing Denial of Service attacks
were only modestly detected by the majority of products. Only
PestPatrol was able to detect any spyware pests." |
|
Use of anti-virus software is not enough, as many
experts have recently argued. "Antivirus software still does an excellent
job of protecting against viruses in the wild; however, other products, in
association with corporate security policy, are now becoming increasingly
important to safeguard the network and critically sensitive corporate
data." - Datapro
Anti-virus technology is not well-suited for detecting
pests
Viruses do not "install" themselves in a machine. They do not normally
examine the registry, nor do they make changes to it. They do not
reconfigure the machine to ensure that they run at next boot. The
challenge with a virus is to remove it from the objects it has infected,
returning them to a fully functional state.
Trojans usually do install themselves in a machine.
They frequently modify the registry, and sometimes also modify .ini files,
such as win.ini. Deleting a trojan will cause a problem if the registry
calls for a missing file to be run. Unlike virus removal, removing a
trojan may require editing the registry.
Because a trojan appears to all intents and purposes
to be a normal uninfected program, and lacks jumps, there is no convenient
section of a few thousand bytes from which a detection scan string might
be extracted. To detect a trojan with a scan string is not difficult. To
do so without false alarming on non-trojans is a great deal more difficult
The PestPatrol approach
PestPatrol scans your system, looking specifically for
malicious code. It currently can detect some 32,000 pests, and the
database continues to grow. PestPatrol is designed to be very fast and can
scan 33,000 files per minute.
How does PestPatrol differ from anti-virus
software?
PestPatrol is not an anti-virus product and it will not remove viruses.
PestPatrol looks for and detects other malicious code, including trojans,
hacker tools, Denial-of-Service attack agents, and spyware. Since
anti-virus products focus on viruses, PestPatrol used in conjunction with
an anti-virus product offers complete and reliable protection from the
full complement of malicious code that might result in downtime, loss of
employee productivity and dissemination of dangerous code.
How does PestPatrol stay current?
We have created a number of tools that automatically manage the PestPatrol
database, trapping new malicious code and constantly updating the
database. Such new files are downloaded and automatically analyzed.
Information on how to remove this malicious code from
the registry, from ini files, and from the file system is automatically
added to our PestPatrol.dat database. The database is automatically posted
to the web site so that users of PestPatrol have access to the latest
strings; the product looks for updates and downloads them automatically,
too. The result: PestPatrol can detect a pest within a few minutes of its
availability on the Internet and have the necessary removal information
immediately available.
Compatibility with anti-virus
PestPatrol is designed to work with anti-virus software, not instead of
it. This design required that several conditions be met:
-
the scanning time for PestPatrol needed to be
lightning fast;
-
the product needed to be "lightweight", taking little
machine overhead;
-
the product needed to detect problems that the
anti-virus software missed, with little overlap.
PestPatrol benefits
PestPatrol is fast because its detection algorithms are specifically built
for pest detection. At the time of writing, the database contains 11
different pieces of information on each of 32,000 different pests - over
350,000 information elements.
PestPatrol is flexible, with powerful command line
capabilities to facilitate scheduling, network-wide scanning (including
systems connecting to corporate servers via VPN), reporting, and updating.
Buy
Now And Get Instant Download ($39.95)
|

